Gpg and linux
Welcome to Simone Giustetti's wiki pages.
Languages: English - Italiano
GPG for Linux
Gnu Privacy Guard is a cryptographic software suite for personal use running on a wide variety of architectures among them the Linux operating system. The standard installation of many distributions includes a GPG package, which is usually regarded as a fundamental tool and as such installed by default. More recent distros include two GPG packages: one for the 1.4.x development branch and a second one for the newer 2.x release. This way users wishing to use the added functionality of the more recent development branch could install the gnupg2 package, while whoever needs to maintain compatibility with old installed machines could install the gnupg package. The basic software functionality and usage will be described in this paper.
Installing GPG
As just said some version of the program is automatically installed by a great majority of Linux distributions. It is still worthwhile to illustrate the installation procedure for when the installation is incomplete or when only a minimal system has been installed in wait for future customizations according to users needs or the installed version is not the one you want. The installation procedure of GPG on Linux varies from other operating systems and even from one distro to another. Basically four major ways to install GPG exist based on the distribution of choice. All of the currently existing Linux distributions share common roots and can be categorized in four main families:
- Debian / Ubuntu
- Gentoo
- Red Hat
- Slackware
The great majority of existing Linux machines feature one of the four listed systems or a system derived from one of them. Specific instructions will be provided for each variant. Installing packages and software on a Linux system requires administrator privileges thus I'll assume you are connected as root from now on.
Installing on Debian
Debian and Ubuntu are among the best known and widespread Linux distributions. Both use packages in the deb format amd manage them with the apt-get command. To install GPG run command:
- apt-get install gnupg
or
- apt-get install gnupg2
The first line of the example installs the old 1.4 release of GPG while the latter installs the newer 2.x release of the software.
Installing on Gentoo
Gentoo differs a lot from other distributions mentioned in this article for two reasons. The first reason being that the distribution does not use version numbers, but it stays in a state of constant update. The second and equally important is that it is a source code based distribution. In other words the majority of the software is compiled from source code during installation. Searching, installing, updating and removing packages is managed through a program named emerge. To install any program run command:
- emerge <program_name>
The system will automatically build and install the package and its related dependencies. The command to install GPG is:
- emerge --ask app-crypt/gnupg
The --ask option will provide a list of the actions performed to update the system before the real installation takes place. installing will start only after a user confirmation.
Installing on Red Hat
Red Hat based Linux systems, CentOS is probably the most famous, use rpm formatted packages recurring to the rpm and yum commands. When properly configured, yum lets you easily install packages using the syntax yum install <package name>. The precise name of the package may vary depending on the distribution used. The 1.4 version of GNU Privacy Guard, for example, could be named gpg or gnupg. Similarly, the name of the packages for version 2.x can vary between gpg2 and gnupg2. To install the package and its dependencies use commands:
- yum install gpg
- yum install gpg2
or
- yum install gnupg
- yum install gnupg2
The former sequence installs GPG version 1.4 while the latter install the newer 2.x software release.
Install on Slackware
The oldest actively developed and maintained among Linux distributions. Slackware uses a very basic approach to system administration and package installation. For a list of installed packages for example you just need to display the content of directory /var/log/packages as below:
- ls -la /var/log/packages
To check whether GPG is installed:
root@system:~# ls -la /var/log/packages/* | grep -i gnupg -rw-r--r-- 1 root root 4467 Aug 19 2015 /var/log/packages/gnupg-1.4.19-x86_64-2_slack14.1 -rw-r--r-- 1 root root 13983 Dec 3 2014 /var/log/packages/gnupg2-2.0.24-x86_64-1_slack14.1 -rw-r--r-- 1 root root 751 Dec 14 2013 /var/log/packages/qca-gnupg-2.0.0_beta3-x86_64-1
In the example above the command returned both a package for the 2.0 release and one for the 1.4; proof that both are available to users. New software is usually installed using the installpkg command. The official packages can be downloaded from the download page of the web site. Download a package for your architecture to a local directory, /tmp for example, then install it with command installpkg <package name>. To install the latest GPG versions for the x86_64 architecture:
- installpkg gnupg-1.4.19-x86_64-2_slack14.1
- installpkg gnupg2-2.0.24-x86_64-1_slack14.1
Omit the first line to install only the latest release of GPG for Linux.
Slackware ships with a tool to automate package management that deals independently with downloads and installing. Slackpkg, the program name, is usually disabled and you need to enable it:
- Update file /etc/slackpkg/mirrors, which contains a list of online mirrors where to download packages from. Set one and only one source by removing the # character from the beginning of the corresponding line.
- Update slackpkg configuration running command:
- slackpkg update
The program will download a list of available packages and some more information needed to configure itself. Then it will be ready to go. Install a package running command slackpkg install <package name> as in the example below concerning GPG:
- slackpkg install gnupg-1.4.19-x86_64-2_slack14.1
- slackpkg install gnupg2-2.0.24-x86_64-1_slack14.1
When done it is possible to configure GPG.
Key Pair and Configuration
Encryption strength relies on a pair of keys. Please read the program documentation before going further. The basic concepts about encryption and GPG internals will be summarized below:
- GPG uses asymmetric cryptography also known as public key cryptography.
- Asymmetric cryptography requires a key pair: a public key, used to encrypt information, and a private key needed to decrypt data.
- A copy of the public key should be delivered to whoever wishes to send you encrypted e-mails or files.
- The private key is secret and should never be shared with anyone.
- Information encrypted with the public key can be decrypted with the private one only.
- The private key can be protected using a passphrase. If stolen, a protected key cannot be used by unauthorized people who do not know the passphrase.
Given the key pair fundamental importance to GPG, it should be created soon after the installation. Key creation will be detailed below. Many graphical interfaces exist in Linux to manage GPG, but no one can be regarded as a standard thus we'll recur to the command line in the examples below.
- Start a terminal emulator such as: xterm or konsole.
I'll describe release 2 of GPG. Were you interested in version 1.4 please replace command gpg2 with gpg. Please note that versions are not fully compatible with one another and some commands cold not work or could produce unexpected results.
- Create the key pair issuing command gpg2 --gen-key
user@system:~$ gpg2 --gen-key
gpg (GnuPG) 2.0.24; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: StudioSG
Email address: studiosg@giustetti.net
Comment: sg_test_03
You selected this USER-ID:
"StudioSG (sg_test_03) <studiosg@giustetti.net>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: key BCB7BBFF marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 2 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 2u
gpg: next trustdb check due at 2018-02-17
pub 2048R/BCB7BBFF 2016-03-17
Key fingerprint = B01C FA65 707E 5096 B91A 825D A4E2 1F27 BCB7 BBFF
uid [ultimate] StudioSG (sg_test_03) <sstudiosg@giustetti.net>
sub 2048R/FA671DAF 2016-03-17
The procedure will ask you to provide a unique identifier and more personal information useful to identify the key.
GPG supports a maximum key length of 4096 bit, but still you are recommended to set the standard value of 2048 bit. The standard length is a good compromise between security and performances and it grants use of external devices like smart cards and such. If you do not need the added benefits granted by a 4096 bit key length, you should probably use the standard 2048 bit value. More information about key format and length are available in the GPG FAQ.
Options standard values are suited for many private and professional use, thus you are strongly suggested not to change them if there is no evident reason to. Do not change option values by trial, be sure to consult the documentation and proceed only when you are sure of the desired result.
You can provide an optional passphrase for the private key during its creation. You are encouraged to always use a passphrase, which safeguards users in case the device where the keys are saved is stolen. A passphrase too short or too trivial cold be discovered by a brute force attack. Use a passphrase longer than 8 characters containing letters, numbers and special characters to defend against such attacks.
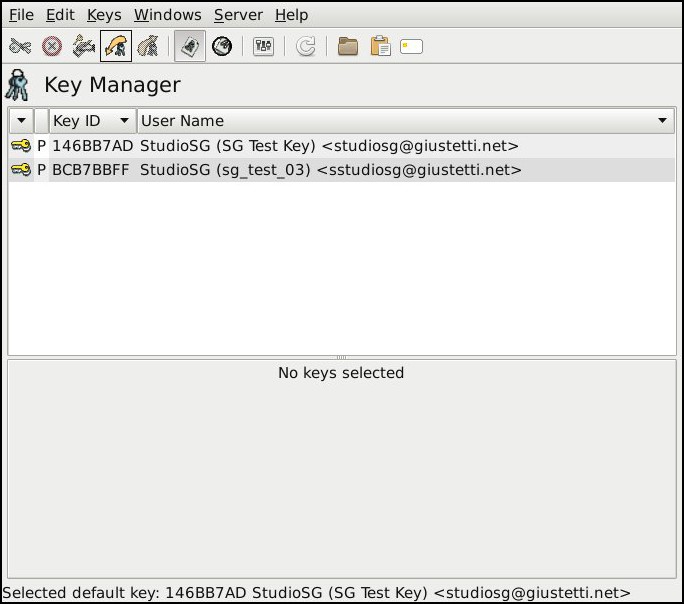
You can obtain a list of existing keys with command gpg2 --list-keys:
user@system:~$ gpg2 --list-keys /home/user/.gnupg/pubring.gpg ----------------------------- pub 2048R/146BB7AD 2016-02-18 [expires: 2018-02-17] uid [ultimate] StudioSG (SG Test Key) <studiosg@giustetti.net> sub 2048R/8FF38CC1 2016-02-18 [expires: 2018-02-17] pub 2048R/BCB7BBFF 2016-03-17 uid [ultimate] StudioSG (sg_test_03) <studiosg@giustetti.net> sub 2048R/FA671DAF 2016-03-17
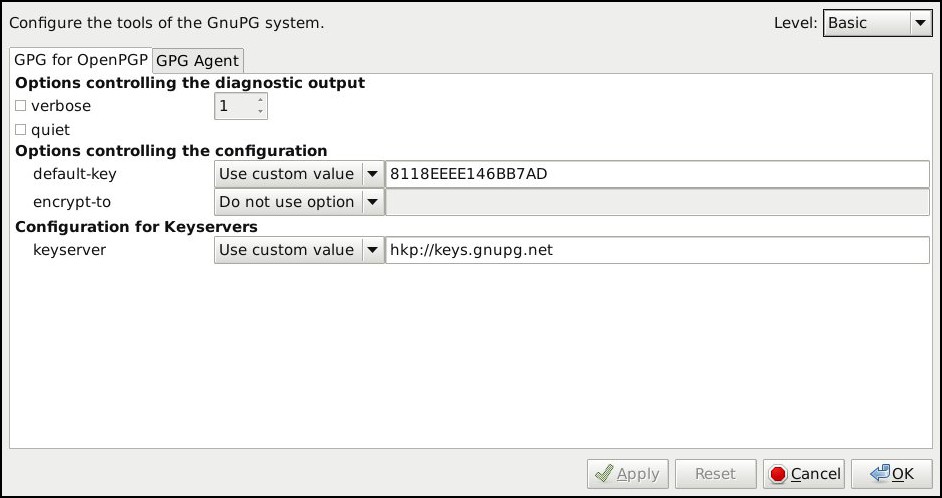
GPG standard behavior can be customized properly setting values for the program options. Configuration options in Linux are saved in text files and can be edited with any text editor. Every configured user has his or her personal copy of the configuration files, which are located in the home directory. The standard GPG configuration file for a user is $HOME/.gnupg/gpg.conf where $HOME is the user home directory. For example, the configuration file of a hypothetical user1 user is: /home/user1/.gnupg/gpg.conf. The dot preceding the .gnupg directory name means that the directory is a hidden one. To list a hidden directory when inspecting the content of its father one use option -a of command ls:
- ls -la
To read or update your own configuration file:
- vi $HOME/.gnupg/gpg.conf
The file is fully commented, but still refer to the program manual for a description of all the options contained therein.
Key Pair Back-up
The key pair is mandatory to open encrypted files: its loss could prove to be catastrophic as currently available processors are not powerful enough to decrypt files without. A whole document archive cold go lost for want of a key. It is a good idea to keep a safety copy of both keys stored in a safe place other than the machine on which you normally work. All keys are stored inside directory $HOME/.gnupg in the form of binary files. A safe and easy way to generate a copy of the key pair consists of creating a password protected compressed archive of the directory:
- tar -pcf key_backup.tar $HOME/.gnupg
- zip -e key_backup.tar.zip key_backup.tar
- rm key_backup.tar
The zip command will ask the user to provide a password for the archive, then to confirm the provided value by retyping it. The resulting archive, key_backup.tar.zip, can be opened only by providing the password.
How-to Encrypt and Decrypt Files
To encrypt or decrypt one or more files with GPG use the --decrypt or --encrypt option of command gpg2 depending on what you wish to accomplish. The base encryption command is:
- gpg2 --encrypt <file>
GPG will ask you to provide the unique identifier for the public key of the file recipient. The key will be used to encrypt the file as in the example below:
user@system:/tmp/_sg_test$ gpg2 --encrypt st_test01.pdf You did not specify a user ID. (you may use "-r") Current recipients: Enter the user ID. End with an empty line: StudioSG Current recipients: 2048R/8FF38CC1 2016-02-18 "StudioSG (SG Test Key) <studiosg@giustetti.net>" Enter the user ID. End with an empty line: user@system:/tmp/_sg_test$
The encrypted file retains the name of the original one but a different extension: .gpg.
You can provide a list of more than one recipient one for each line. An empty line of text marks the archive end. A list of saved keys available to encrypt files can be retrieved recurring to the --list-keys option:
user@system:/tmp/_sg_test$ gpg2 --list-keys ----------------------------- pub 2048R/146BB7AD 2016-02-18 [expires: 2018-02-17] uid [ultimate] StudioSG (SG Test Key) <studiosg@giustetti.net> sub 2048R/8FF38CC1 2016-02-18 [expires: 2018-02-17] pub 2048R/BCB7BBFF 2016-03-17 uid [ultimate] StudioSG (sg_test_03) <studiosg@giustetti.net> sub 2048R/FA671DAF 2016-03-17
You can encrypt many files at once recurring to the --multi option. You'll have to provide a recipients list for each file. This could prove to be a lot of work and GPG provides option -r to simplify it. Using -r the recipient list can be appended to the command line. In the example below three documents are encrypted using the key of recipient StudioSG:
user@system:/tmp/_sg_test$ ls -la total 48 drwxrwxrwx 3 user1 users 4096 Mar 18 18:50 ./ drwxrwxrwt 17 root root 4096 Mar 18 18:37 ../ -rw-r--r-- 1 user users 7737 Mar 18 18:50 st_test01.pdf -rw-r--r-- 1 user users 7844 Mar 18 18:50 st_test02.pdf -rw-r--r-- 1 user users 7932 Mar 18 18:50 st_test03.pdf user@system:/tmp/_sg_test$ gpg2 -r StudioSG --multi --encrypt st_test0* user@system:/tmp/_sg_test$ ls -la total 72 drwxrwxrwx 3 user users 4096 Mar 18 18:50 ./ drwxrwxrwt 17 root root 4096 Mar 18 18:37 ../ -rw-r--r-- 1 user users 7737 Mar 18 18:50 st_test01.pdf -rw-r--r-- 1 user users 7378 Mar 18 18:50 st_test01.pdf.gpg -rw-r--r-- 1 user users 7844 Mar 18 18:50 st_test02.pdf -rw-r--r-- 1 user users 7487 Mar 18 18:50 st_test02.pdf.gpg -rw-r--r-- 1 user users 7932 Mar 18 18:50 st_test03.pdf -rw-r--r-- 1 user users 7574 Mar 18 18:50 st_test03.pdf.gpg
You can decrypt a file with the --decrypt option of the gpg2 command. GPG will prompt you for a password and, once inserted, will output the "clear text" content of the encrypted file on the standard output. To save a decrypted version of the file the --output option and the name of the saved file are required:
- gpg2 --output <clear text file> --decrypt <encrypted file>
user@system:/tmp/_sg_test$ gpg2 --output st_test01.pdf --decrypt st_test01.pdf.gpg
You need a passphrase to unlock the secret key for
user: "StudioSG (SG Test Key) <studiosg@giustetti.net>"
2048-bit RSA key, ID 8FF38CC1, created 2016-02-18 (main key ID 146BB7AD)
gpg: can't connect to the agent - trying fall back
gpg: encrypted with 2048-bit RSA key, ID 8FF38CC1, created 2016-02-18
"StudioSG (SG Test Key) <studiosg@giustetti.net>"
user1@system:/tmp/_sg_test$ ls -la
total 56
drwxrwxrwx 3 user users 4096 Mar 18 19:21 ./
drwxrwxrwt 17 root root 4096 Mar 18 19:14 ../
-rw-r--r-- 1 user users 7737 Mar 18 19:21 st_test01.pdf
-rw-r--r-- 1 user users 7378 Mar 18 18:50 st_test01.pdf.gpg
-rw-r--r-- 1 user users 7487 Mar 18 18:50 st_test02.pdf.gpg
-rw-r--r-- 1 user users 7574 Mar 18 18:50 st_test03.pdf.gpg
GPG-AGENT
Gpg-agent is a daemon that stores in an internal cache all of the user provided passphrases and later forwards them to all programs asking for one. You basically have to insert any password only once and not each time a document is opened. The time saving is considerable for the staff of an office that needs to read and handle large amounts of documents every day.
The daemon must be up and running to store passwords and the environment must be properly configured in order for programs to know of the daemon existence and to query it when needed. Linux is a complex environment where both a graphical interface and a command line one are available and can be used for configuration tasks. Another factor to consider is that more than one shell exist for the command line interface and users can use any to run a command. Shells can be interactive, ie actively operated by a user, or not, as is the case of scripts that execute commands in an autonomous way. A way to be sure that gpg-agent will be available to all of the cli commands is to launch it when the shell starts.
You can start the agent with command:
- /usr/bin/gpg-agent --sh --daemon --write-env-file $HOME/.cache/gpg-agent-info
The above line should be added to the shell configuration file in order for gpg-agent to be started automatically. For the bash shell, the Linux default one, a couple of configuration files exist:
- $HOME/.bash_profile or $HOME/.profile used by a login shell namely the one used to connect to an host.
- $HOME/.bash_rc for a no login shell, a secondary interpreter started from within a login shell once you are connected to the host.
An example of start-up commands is available below:
# Start gpg-agent at login
# Check whether the daemon is running
if test -f $HOME/.cache/.gpg-agent-info && \
kill -0 `cut -d: -f 2 $HOME/.cache/.gpg-agent-info` 2>/dev/null; then
GPG_AGENT_INFO=`cat $HOME/.cache/.gpg-agent-info | cut -c 16-`
else
# gpg-agent is down => Start it
eval `gpg-agent --daemon --sh --write-env-file $HOME/.cache/.gpg-agent-info`
fi
# Set the environment variables
GPG_TTY=$(tty)
export GPG_TTY
export GPG_AGENT_INFO
For a ksh, zsh or other shell, the configuration file read at start-up varies. Append the commands presented above to the proper file. Please consult the documentation of your shell of choice for detailed information about its configuration.
A variety of graphical interfaces are available on Linux: Gnome, KDE, TDE, Xfce, luckily the configuration is more or less standardized if compared to the cli as many offered services share a common root: the | X Window System. To automatically start gpg-agent you can edit the $HOME/.xinitrc file containing the boot options for a X session. An example of the line to add to the file to inform the desktop environment of the presence of gpg-agent ia available below:
eval "$(gpg-agent --daemon)"
The added line will enable running programs within a session to query gpg-agent for its services.
Gpg-agent configuration parameters are stored into file $HOME/.gnupg/gpg-agent.conf. Among them default-cache-ttl is worth mentioning as it sets the interval of time a password is kept in the cache. Beyond that limit the password will be removed and re-asked the user in case of need. The standard time to live of a password amounts to 600 seconds or 10 minutes. To increase this interval to one hour change line
default-cache-ttl 600
in
default-cache-ttl 3600
then restart the gpg-agent daemon.
Graphical Interfaces
There are several graphical interfaces aimed at administering GPG on Linux. Most of the interfaces are integrated with the graphical environment in use such as Kgpg for KDE 4, or Kleopatra a multi-platform interface available for Linux and other Unixes and even for Windows. All programs provide the same functionality and share a similar appearance. However, there are differences arising from the level of integration with the environment for which they are developed and we recommend that you review the documentation for each of them. The standard GPG package includes Gpa as default interface. They are usually installed together:
With Gpa you can create key pairs, encrypt and decrypt files and set options for GPG or gpg-agent:
All of the procedures previously details for the command line interface can be accomplished through Gpa.
Conclusions
This paper provides a brief description of the Linux versions of GNU Privacy Guard. The installation and the basic operation of the program were described trying to be as much distribution neutral as possible. The last part of the article provides a hint to the many graphical interfaces available to configure the software and its related services. For more information you are encouraged to read the manual and the many articles available on the net and in this very same website. Were You interested in our offerings or simply looking for more information, please refer to our contacts page. Thank You.
To contact me or leave me your feedback, Please e-mail at studiosg [at] giustetti [dot] net.
External links
Languages: English - Italiano